Passwords: from setting up your first AOL account to completing a banking transaction on your cell, these applications have all had them. But the enduring use of passwords may soon become a thing of the past.
At Thursday’s GovLoop Training, Ensuring Safe Access for Government Users: The Evolution of Identity Management, we talked with Dan Waddell, Director of Government Affairs, (ISC)2, and Kolin Whitley, Director, Fraud & Identity Solutions, Decision Analytics, Experian, to learn why password protection is outdated and how the future of identity relationship management (IRM) will help us stay secure.
Remembering your vast collection of passwords is difficult, while using the same one for all your accounts leaves you especially vulnerable. And with major data breaches occurring on an increasingly frequent basis, much of this data is likely already compromised. “Passwords are the root of many evils,” Waddell said, referring to recent breaches at JP Morgan, Apple, and the U.S. Postal Service where passwords were central to the hacks.
And now with the Internet of Things where devices and even houses, refrigerators, and cars are all connected, access management and security is even more difficult. Ten or more devices in American homes have an IP address, said Waddell, and that average is growing every year. As consumers look for convenient ways to remember their new account passwords – “12345” or “password” passwords, repeated use, storing in one place – the hacker’s job gets easier and easier. This is why it is critical to find new ways to access accounts/products without the traditional user name and password set-up.
In response to these concerns, the National Strategy for Trusted Identities in Cyberspace (NSTIC) laid out the follow four guiding principles for identity management:
#1. Privacy-enhancing and voluntary
When doing business with government, information needs to be trusted. It must have acceptable use terms and there must be clear guidelines about who is managing and storing your information and how.
#2. Secure and resilient
Resiliency is critical in information security. Whatever solution an agency has, it must be able to withstand time and be up and running in the event of a disaster or practical breakdown.
#3. Interoperable
This involves having different databases across several agencies and allowing those databases to collapse into one record or account – a single sign-on mechanism.
#4. Cost-effective and easy to use
If the solution is too difficult or complex, the user will circumvent and try to find an easier, and thus more vulnerable, way to manage identity information.
NSTIC also calls for an identity ecosystem, described as:
“An online environment where individuals and organizations will be able to trust each other because they follow agreed upon standards to obtain and authenticate their digital identities.”
Furthermore, in an October Executive Order, President Obama called for “all agencies making personal data accessible to citizens through digital applications” to “require the use of multiple factors of authentication and an effective identity proofing process.”
These initiatives illustrate the current relevance and importance of identity relationship management (IRM) in the digital age. But how do you increase security, while maintaining user convenience? IDaaS may provide the answer.
IRM to IDaaS
Kolin Whitley of Experian explained a slightly different approach to the same topic, looking at identity as a service (IDaas). Wherein IRM focuses on managing the connection of people, places, and things, IDaaS represents the umbrella of activities and solutions that support and enable this management through its lifecycle. IDaaS includes basic activities such as password reset and attribute verification as well as more comprehensive solutions such as multi-factored authentication, biometrics (fingerprints, retina scans), and linkage analysis between identities and devices. IDaaS is essentially any service that provides a trust relationship between people and devices, said Whitley.
Identity as a service helps meet the demand of citizens and customers, who expect their personal information to be protected from unauthorized access. But at the same time, this security shouldn’t be overly burdensome to users. “Frictionless customer interaction and authentication through the customer lifecycle is now a competitive requirement,” said Whitley. Experian blends protection and convenience in an ongoing four-step process:
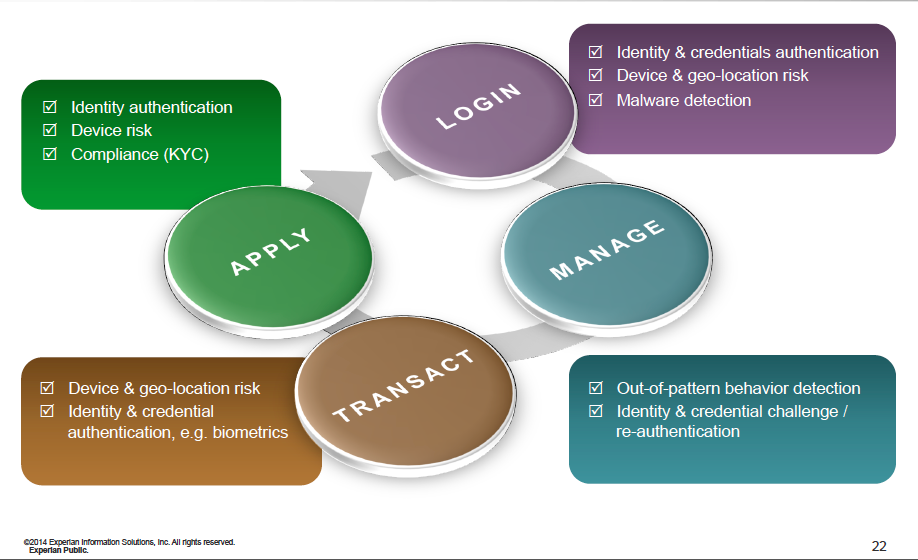
Verifying identify on an ongoing basis – with mechanisms such as geo-location – is key, especially to determine changes and events that may represent a risk.
Getting Started
Our speakers predict in the next three to four years, IDaaS will become more fully realized and authentication services will allow seamless, single credentials that can be used across multiple applications. Therefore, getting ahead of the IRM curve can prove beneficial.
Resources from NSTIC and GSA can help prepare your agency for the future of identity management in the post-password era. It’s also important to communicate and work with industry partners – NSTIC won’t succeed without this collaboration, Waddell said.
For more information, check out the full presentation.
Do you have any other tips or resources for effective identity management solutions? Please share below!

Photo Credit: Flickr, Dev.Arka.




Leave a Reply
You must be logged in to post a comment.