By now, you may have already migrated some applications to a cloud environment, or you may be just starting. An underlying question, is the cloud safer for your data and applications than on-premises? That depends. Minimally for your data, there are two actions to incorporate in your approach:
- Encryption in transit
- Encryption at rest

Of course, this only protects your data, so the next step is to protect your application. Focusing on the security aspect, there are several approaches for perimeter-based security (a subcomponent of a secure access service edge model).
So, one or multiple clouds? If your cloud environment needs are met with one cloud, then your security approach may be satisfied using that cloud vendor’s security offerings. As you branch out from more than one cloud, using each cloud vendor’s security approaches could leave you vulnerable, as it will be difficult to simultaneously address security concerns. In a multi-cloud scenario, your approach should consider utilizing a single security management console to provide:
- Simultaneous visibility into multiple clouds.
- Simultaneous mechanisms to deliver patches and/or blocks for multiple virtual firewalls.
Features of virtual firewalls to consider:
- Machine learning capabilities to continue analysis and applying blocks as needed
- Zero-day signature updates
- Policy-based controls (e.g., User ID, App ID, Content ID, etc.)
Consider a scenario of one or more application environments (referred to as being contained in a virtual private cloud or VPC) in a public cloud vendor. One approach is to create an additional VPC dedicated to security where it contains the firewalls for those applications. All access into and out of all VPCs route through this security VPC. Within the security VPC, you will minimally want to have two virtual firewalls set up in a high availability (HA) configuration. Check these as well:
- Does the firewall licensing provide sufficient bandwidth for network traffic?
- Is the underlying infrastructure robust enough for the virtual firewall?
A design consideration is to have each virtual firewall in a separate availability zone (AZ) within a region (your cloud vendor’s terminology may vary), ensuring HA needs are met. The connection from the security VPC to all the application environments will be via a managed router or gateway. The high-level diagram could resemble this:
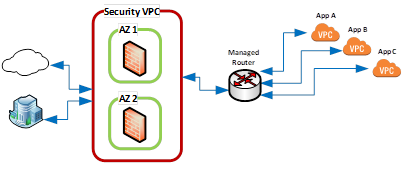
Your final version may be different, which is OK. The diagram reflects the suggestions above where the firewalls reside in separate AZs and the security VPC connects to the cloud vendor’s managed router providing access to the application VPCs. Different configurations can be considered (e.g., one to handle incoming traffic, one to handle outgoing traffic). Just ensure the underlying design is set up as HA as the underlying hardware will fail at some point. Will this suffice to secure all your cloud environment? Well, possibly. Will it provide a foundation to build from? Yes, it should, but consider some of your cloud vendor’s security solutions and how many additional layers of security protection are needed for your business team’s different data/application sets
Dan Kempton is the Sr. IT Advisor at North Carolina Department of Information Technology. An accomplished IT executive with over 35 years of experience, Dan has worked nearly equally in the private sector, including startups and mid-to-large scale companies, and the public sector. His Bachelor’s and Master’s degrees in Computer Science fuel his curiosity about adopting and incorporating technology to reach business goals. His experience spans various technical areas including system architecture and applications. He has served on multiple technology advisory boards, ANSI committees, and he is currently an Adjunct Professor at the Industrial & Systems Engineering school at NC State University. He reports directly to the CIO for North Carolina, providing technical insight and guidance on how emerging technologies could address the state’s challenges.





Leave a Reply
You must be logged in to post a comment.