“There are two kinds of CIOs: ones who have been hacked and know it, and those that have been hacked and don’t realize it yet. But the reality is, you’ve been hacked.” This is a startling statement from Tony Scott, the CIO of the Office of Management and Budget, that emphasizes the massive cyberthreat to your agency’s data security. GovLoop’s recent online training helped data owners explore tools that support organizational initiatives where critical data can be breached and explained how to successfully implement DHS’s Continuous Diagnostics and Mitigation (CDM) program into your agency.
Our panelists included:
- James Quinn, Lead System Engineer CDM, Department of Homeland Security
- Wayne Lewandowski, Area Vice President, Federal, Vormetric
The training, CDM: Securing the Data, Not Just the Perimeter, addressed numerous concerns and solutions to implement a governance policy and enable technology to secure data for the data owner.
Continuous Diagnostics and Mitigation
With cyberthreats coming at government organizations so frequently, agency leaders consider the lack of a cyber procurement system to be a major problem. They need a system that is adaptive and responsive to cyber attacks and data breaches. Essentially, to establish the priorities of your agency’s CDM governance, your IT staff and leaders should rank the importance of data and where it can be accessed to comply with guidelines and protect important information.
The program objectives of CDM are to establish a consistent, government-wide set of information security continuous monitoring tools to protect “.gov” domains. The program will also combine the buying power of civilian agencies to achieve cost efficiencies for cyber security tools, saving agencies valuable funding. CDM will provide dashboards to improve situational awareness and enhance agencies’ ability to identify and respond to the risk of emerging cyber threats. But where does your agency begin?
The three phases of CDM outline a detailed model to implement a shift to data security governance in a manageable way. Once infused into agency culture, CDM will allow agencies to grow technologically by allowing users to access information quickly, collaboratively, and – most importantly – securely. While this information can be daunting and technical, Homeland Security’s James Quinn broke down the information to make meeting standards a reality for your organization.
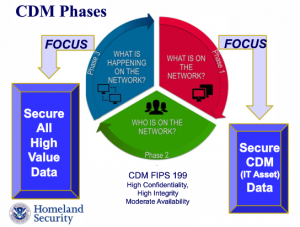
Shift in Security
The responsibilities of individuals in agencies play a large role in determining the security of data and distinguishing what people have access to what data. By ranking organizational priorities based on risk, your agency can make a significant step toward protecting data.
As government organizations continue the trend of pursing technology options that make information and data more accessible, effective governance needs to be in place to protect data. This specifically includes data that can be accessed remotely, on different servers, and on varying storage platforms like the cloud. Check out this helpful resource below from the training to identify at-risk data locations that need to be addressed for security purposes.
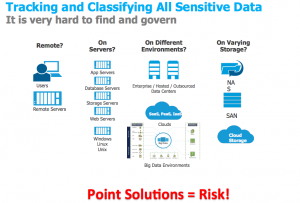
By implementing the CDM program and internally prioritizing agency data, agencies can make great stride in protecting themselves from cyber attacks. The CDM program benefits will also include centralizing governance by the data owner, rather than the host, determining role based and security groups for data access, an the ability to provide granular access controls. But overall, the major outcome of complying with CDM standards is protecting agencies from critical breaches involving compromised privileged accounts. This will save your agency the ordeal and embarrassment of suffering through a data breach.
Want to learn more about securing your data against cyber attacks and complying with CDM standards? View the entire online training on-demand!





Leave a Reply
You must be logged in to post a comment.