Traditionally, organizations took a moat-and-castle approach to network security: Anything within a network’s perimeter was deemed safe, while external infrastructure and activity raised cybersecurity concerns.
But that approach has proven costly and insufficient as cyber criminals devise new schemes to invade our networks and traditional on-premises systems become more scattered and diffuse.
So, the federal government, some local governments and much of the private sector now are transitioning to a zero-trust architecture. It essentially turns traditional cybersecurity on its head.
Rather than worry about perimeters, zero trust by default denies people access to enterprise information. Users are granted limited access based on their roles and responsibilities, and no one or device is implicitly trusted.
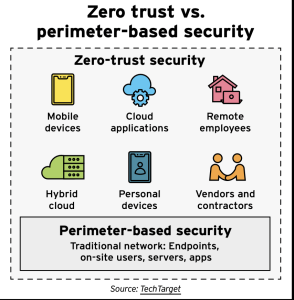
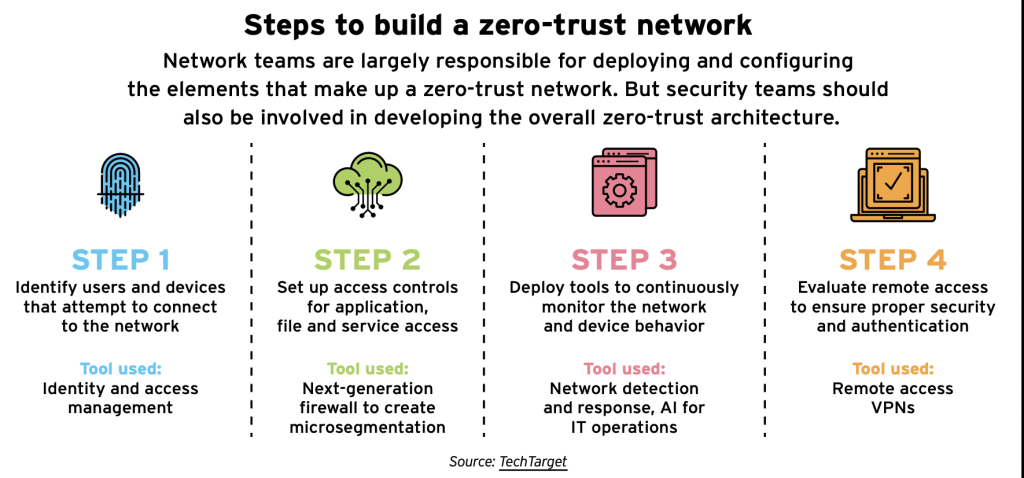
The framework relies on multi-factor authentication, encryption, and continuous monitoring and verification, among other features. Transitioning to a zero-trust architecture can be costly, though, and it takes time.
But it’s critical. “Incremental improvements will not give us the security we need,” said the Administration in a May 2021 executive order. “Instead, the Federal Government needs to make bold changes and significant investments in order to defend the vital institutions that underpin the American way of life.”
“A transition to a ‘zero trust’ approach to security,” the EO continued, “provides a defensible architecture for this new environment.”
This article appeared in our guide, “A New Cyber Game Plan Takes Shape.” To learn more about how respond to — and head off — the latest threats, download the guide:





Leave a Reply
You must be logged in to post a comment.