This blog post is an excerpt from GovLoop’s industry perspective: Making the Most of FedRAMP. Download the full report here.
FedRAMP is about more than standardizing cloud security across government. One of the biggest benefits it provides is the ability for agencies to reuse and build on one another’s work.
Rather than each agency re-evaluating the same cloud services, they can share notes and ask questions to determine if those services meet their needs. The premise of FedRAMP is that the baseline standards it provides cover requirements that are common across agencies. That frees agencies up to focus on the few requirements that may be unique to them.
“Individual agencies can accept their own level of risk associated with a cloud service when authorizing that cloud service (as allowed by the Federal Information Security Management Act), [but] one agency may be hesitant to reuse another agency’s authorized cloud solution because it may not trust the risk tolerance associated with that authorized cloud solution,” Ashley Mahan, FedRAMP Agency Evangelist, told GovLoop.
To help ease these concerns, she said that FedRAMP is supporting agencies to:
Provide high-level education about the cloud, security and the FedRAMP program.
Standardize the documentation and review process. FedRAMP encourages agencies to perform their due diligence in reviewing all security documentation that is located within the FedRAMP secure repository prior to issuing an authorization.
Clarify the risks that the authorizing agency accepted. FedRAMP is applying safeguards to ensure agencies are well informed prior to reusing an agency-sponsored Authority to Operate (ATO). The FedRAMP team reviews each sponsored agency standard ATO package and provides a summary report (three to four pages) outlining the system risk to ensure each agency makes an informed review and decision. FedRAMP retains a copy of all authorized cloud service providers’ security documentation and assists agencies in performing their due diligence in reviewing all security documentation.
Agencies have been shouldering more of the responsibilities of working directly with cloud providers to complete the authorization process. Initially, the FedRAMP Joint Authorization Board (JAB), the program’s primary decision-making body, 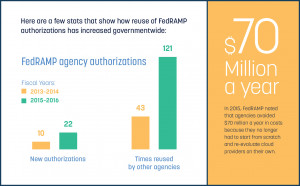 had that task.
had that task.
“From the beginning, we’ve always said the vast majority of authorizations should go through agencies,” FedRAMP Director Matt Goodrich said at a government cloud computing conference. “They should not be going through the Joint Authorization Board. The Joint Authorization Board has limited funding. When we launched FedRAMP, every agency said, ‘We don’t want the department of FedRAMP. We don’t want everything to go through one centralized placed. We still want some control over the IT that we manage and that we buy and use.’”
But products and services used broadly governmentwide are ideal candidates for the JAB.
Federal agencies can review FedRAMP authorization packages through the secured document repository on the OMB Max website. State employees are not allowed to review FedRAMP security documentation, but they are encouraged to contact any FedRAMP-authorized provider directly to learn about their security package specifications.
The best approach for government is to engage vendors early in the process when they’re considering moving to the cloud, so that they understand what’s included and excluded from the FedRAMP security package. This documentation outlines how a company’s security practices align with FedRAMP requirements.
When reviewing the package, agencies should consider whether the security controls outlined meet agency requirements. Other tips from FedRAMP.gov include focusing on whether the agency that did the initial authorization is using the system in the same manner as your agency and if the data being stored in the cloud requires the same level of security.
“Before you ever get to the procurement cycle, it’s good to review the FedRAMP package and then come to the cloud service provider with your questions and ask for clarification or for more detail,” said Andy Campbell, Business Development Manager of Cisco’s U.S. Public Sector, Regulated Cloud.
Some agencies have waited until the procurement phase to ask questions and divulge their terms and conditions for data security that vendors are expected to follow. Delaying these discussions creates unnecessary burdens and setbacks for the agency.
To prevent these issues, agencies need to have the right people at the table to review a cloud provider’s security plan and ask any pertinent questions early on.
Campbell suggests including the agency’s security team, particularly the chief information security officer and chief information officer, who ultimately authorize that a cloud service is OK for use within the agency, as well as procurement officials and your agency’s general counsel.






Leave a Reply
You must be logged in to post a comment.