 Usually, the first task on a new Chief Information Security Officer’s (CISO) 30-, 60- or 90-day plan is to develop an effective team and/or organization. An effective and aligned organization will help the CISO improve its cybersecurity posture and reduce the risk to its business operations. There is no standard toolbox to approach these items, but this article will provide some guard rails to assist in this critical task by using the organization’s basic cybersecurity requirements and then providing a model. The model can be adjusted to meet your organization’s unique needs and can be justified based on its size, revenue and employee count.
Usually, the first task on a new Chief Information Security Officer’s (CISO) 30-, 60- or 90-day plan is to develop an effective team and/or organization. An effective and aligned organization will help the CISO improve its cybersecurity posture and reduce the risk to its business operations. There is no standard toolbox to approach these items, but this article will provide some guard rails to assist in this critical task by using the organization’s basic cybersecurity requirements and then providing a model. The model can be adjusted to meet your organization’s unique needs and can be justified based on its size, revenue and employee count.

Table 1: Cybersecurity Domain vs. Organization size matrix (guidance only)
The above table displays a matrix of key cybersecurity domains vs. organization size. Please note that this is a high-level matrix and should only be used for guidance. Each organization has unique cybersecurity requirements, and this guidance will assist in designing and developing a baseline framework to meet their needs. The dots may move across to address unique needs. Please note for small organizations, there is usually one FTE (Full Time Equivalent) who manages all cybersecurity assignments, or it is staffed by an existing IT staff.
Irrespective of the size, there are a few critical roles that should be prioritized for maintaining a basic cybersecurity posture.
Critical Roles:
- Risk Assessment & Management – Risk assessment and management are the key aspects of the cybersecurity organization. It can vary from using a simple assessment tools (CSAT from the Center of Internet Security) to utilizing a Governance Risk and Compliance (GRC) platform. This is a baseline and critical role within the cyber organization.
- Security Operations – This important role has multiple assignments varying based on the size of an organization and also the revenue. These include incidence management, data security, threat monitoring, and infrastructure and network security. These assignments are displayed in Table 1.
- Cyber Security Architect/Analyst – Regardless of the size of the organization, a security reference architecture can be easily established by this role. The role also maintains awareness and training which is a critical requirement when working from home is the new normal. This role can act as a liaison to other departments to improve the cybersecurity posture.
Please refer to the organizational models illustrated in Figure 1 for expanded version of these roles.
Partnerships:
There is a constant demand to “do more with less,” especially during the COVID-19 pandemic, which has impacted the revenue streams for all industry verticals. To counter this challenge, partnerships to leverage skills and experience within the ecosystem are very important. The ecosystem includes internal partners (infrastructure, application development, shared services, etc.) and external partners (vendors, managed service providers, etc.). There are visible advantages in establishing pipelines with local higher educational institutions offering cybersecurity education by offering internships and starting analyst positions.
Sustainability:
Sustainability is equally important due to attrition and lack of talented resources in cybersecurity. Rotating assignments and roles will keep the employee motivated and challenged. I also recommend that the leaders use concepts from high-performance team building to nurture and grow the cybersecurity organization.
The figure below displays sample organizational structures for a typical small, medium and large cybersecurity organization. Please note that these illustrations are for guidance only based on the domains listed in Table 1. Individual organizational needs may impact the actual organizational structure. The figure also displays relationships with managed service providers providing essential cyber operations support based on the hybrid model.
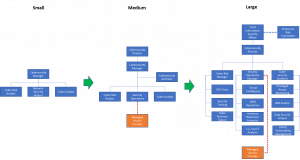
Figure 1: Sample organizational charts for small, medium and large cybersecurity organizations
Key Takeaways:
- Start small and recruit qualified candidates. Use local educational institutions for a pipeline to the starter roles.
- Train, train and train! Keeping the skills up to date and job rotation ensures that the employees are challenged and motivated.
- Leverage partnerships with vendors and peer organizations to meet your organizational needs.
Rajiv has more than 25 years of information technology strategy, operations, large systems integration, cyber security and program management experience. Rajiv is a principal with Plante Moran management Consulting, cybersecurity practice after serving as Chief Information Security Officer (CISO) for the Department of Technology, Management and Budget, State of Michigan.





Leave a Reply
You must be logged in to post a comment.