Data collection and organization are important steps in becoming more data-centric. And for data to truly be useful, it should be accessible to everyone who needs it.
Without access to the right data, agency leaders and employees won’t have the information and perspective they need to make effective decisions.
GovLoop teamed with MarkLogic, a data management software company, to survey agencies about their data goals; and to explore how agencies can use the DoD Data Strategy as a blueprint for their own data strategy.
More than 77% of survey respondents considered it important for agency data to be available to users as needed (see figure 3 to the right).
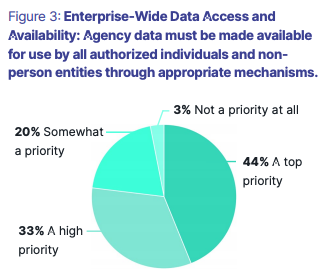
Getting the right information to the right people might seem easy, but privacy and governance, along with security concerns and policies, can complicate the issue. These complexities are probably why the DoD Data Strategy put it this way: “DoD data must be made available for use by all authorized individuals and non-person entities through appropriate mechanisms.”
“The goal is for people to have access to the data they need to do their job when they need it, but at the same time, you need to make sure that only people with the right credentials can access the data and prevent people without permission from doing so,” said Kim Kok, Vice President of Sales for Public Sector at MarkLogic.
The first step in ensuring safe accessibility is to harmonize data from different sources into a data hub that serves as an authoritative data repository for cross-functional discovery. An enterprise data hub can serve as a real-time, data-centric interchange supporting analysis, discovery and operations throughout the data life cycle.
Agencies can take several steps to ensure that only users with the right credentials can access the data, including:
- Ensuring that any platform you use incorporates technologies such as role-based access control, where each user is assigned appropriate roles, each associated with specific privileges and permissions. Privileges govern the creation of documents and execution of functions, while permissions indicate what users can do with a document, such as update, read, insert or execute.
- Ensuring that your platform conducts frequent security checks, which verify the necessary credentials before granting the requested action.
- Using Attribute-Based Access Control and Policy-Based Access Control, which can further restrict access. Restrictions are based on attributes such as time of day and location, with policy information stored in document metadata, or with labels representing high or low levels of trust.
These methods are particularly helpful when multiple stakeholders are involved. For example, some federal agencies must share data with state and local agencies in areas such as health care and first response. Although sharing is critical, it’s equally important to ensure that only authorized personnel can access specific datasets.
This article is an excerpt from GovLoop’s recent report, “How to Take a Page from DoD’s Data Strategy.” Download the full report to learn how to revamp your enterprise data strategies and what lessons you can take from DoD’s approach here.
Photo credit: Defense Department Flickr





Leave a Reply
You must be logged in to post a comment.