If you were feeling a little unsettled about possibly missing a list of “all-things cybersecurity products” offered on GovLoop’s “From Framework to Action: Understanding the NIST Cybersecurity Framework” online training yesterday, I’m here to tell you that it may be time for your security posture check-up.
“The idea of security being a certification or a checkbox that can be achieved nearly by buying certain things has gone away,” said Paul Christman, Vice President of Dell Software’s Public Sector. “Security is a technique or condition which is achieved through continuous inspection and improvement.”
Paul, along with the other expert panelists; Danielle Kriz, Director of Global Cybersecurity Policy Information Technology (ITI) and Matthew Barrett, Program Manager at National Institutes of Standards and Technology (NIST), helped us identify the characteristics and value of the cybersecurity Framework developed by NIST (and consisting of 102 subcategories and best practices).
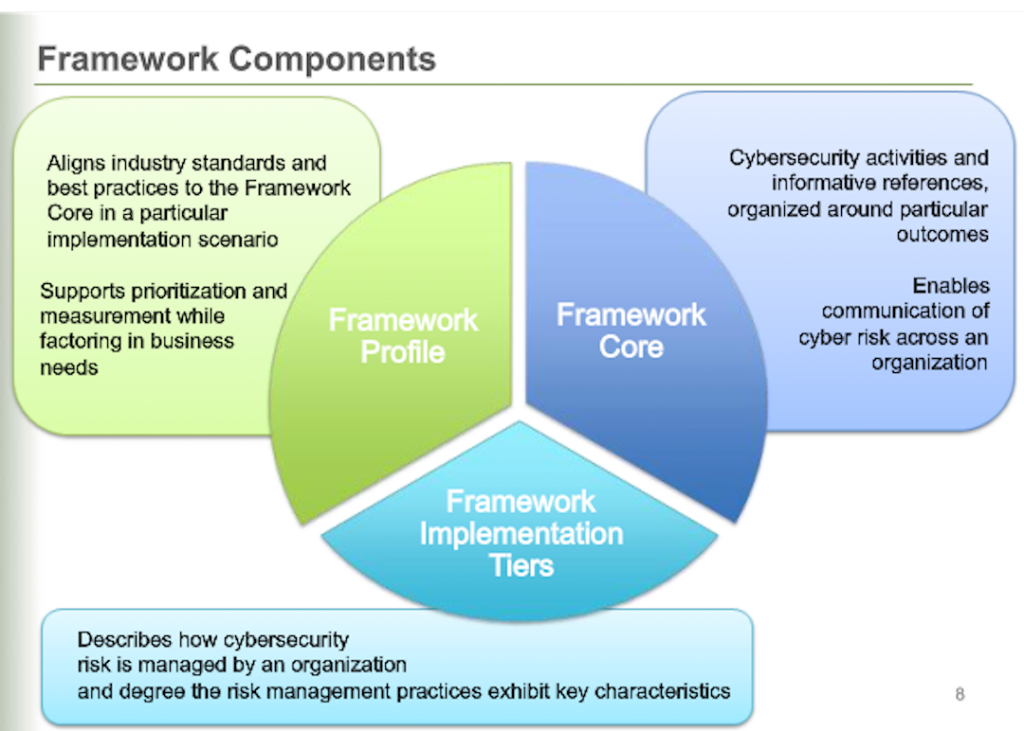
Matthew Barrett started off the discussion by explaining the Framework’s core, profile and tiers in order to convert the 9% of attendees who said they had no plans to use the framework anytime soon. The core consists of five functions with a ripple-down effect that serves as a mechanism to the risk manifest in miscommunication. The profile, which establishes a roadmap for reducing cybersecurity risk, describes current state or desired state by applying the framework core for gap analysis. And the tiers, facilitates trade-off dialogue to build on what is most important for each organization. Together, these three principals – core, profile and tiers — are not a prescription, but an opportunity for a healthy inspection, or proven plan, to move your organization into a much more secure environment. As the speakers noted, not all organizations are meant to follow every piece of the Framework.
Danielle Kriz, from ITI, shared how the Framework’s ability to preserve innovation, because of it’s voluntary flexibility and global standards view, is valuable in order to keep up with the changing threats and technology. ITI supports its use throughout federal agencies and with a neutral mission. Kriz noted the value of the Framework is that it leverages public-private partnerships and works to eliminate the information gap that stems from some organizations leveraging the best practices identified in the Framework, and some not. “The Framework will help improve cybersecurity, and we are committed to helping it succeed,” said Kriz. According to our attendees, 61% said budget constraints were the biggest problem to achieving holistic cybersecurity. But understand adopting the Framework can be an important first step to improving security.
Navigating the NIST Framework is fairly simple if organizations take the time to comb through the information. The framework can be explained in a universal language, making it a wonderful way to start the discussion with stakeholders (non-techies with access to people and money). Paul Christman recommends taking seven steps to finding security blind spots and making the framework extensible:
- Prioritize and scope mission objectives and priorities.
- Match critical systems with threats.
- Create a current cybersecurity technology profile based on Framework categories.
- Conduct a risk assessment.
- Create a target profile of the organization’s desired state.
- Determine, analyze, and prioritize gaps between mission priorities, critical systems, current technology profile, desired, state, and risks.
- Develop a strategy to address the items uncovered in step 6.
If you’re feeling good and asking, “what if I’m already very secure?” think of the Framework as a check-up to see what you have accomplished. Learn more about how NIST developed the Framework and ITI’s Work on Cybersecurity by listening to the on-demand version here.
Want more information? Download the report Navigating the NIST Cybersecurity Framework.






Leave a Reply
You must be logged in to post a comment.