Operational Excellence!
 This is the third part of my thoughts on a Chief Information Security Officer’s 365-day journey. As you have previously observed in the first two parts (Part 1 and Part 2), the focus was on establishing a cybersecurity framework, initiating a foundational program and developing the human capital side of the organization. By the third quarter of operation, the focus should be on operational excellence. In simple terms, what is working and what is not! This is the appropriate time to adjust the cyber strategy and operational components based on the lessons learned in the first to 90-day segments.
This is the third part of my thoughts on a Chief Information Security Officer’s 365-day journey. As you have previously observed in the first two parts (Part 1 and Part 2), the focus was on establishing a cybersecurity framework, initiating a foundational program and developing the human capital side of the organization. By the third quarter of operation, the focus should be on operational excellence. In simple terms, what is working and what is not! This is the appropriate time to adjust the cyber strategy and operational components based on the lessons learned in the first to 90-day segments.
Continuous Improvement Journey
I am a firm believer of the “Kaizen” philosophy, which combines two words: “Kai” (improvement) and “Zen” (good). This translates to continuous improvement. The first two 4/10 phases have focused on improvement & good, and this phase takes a checkpoint in keeping up with the continuous improvement concept as illustrated in Figure 1. The third phase typically consists of the strategic and operational activities as displayed in Figure 2.
Figure 1: Continuous Improvement Cycle
Third Quarter Goals (Operational Excellence)
Checkpoint for Assessment Gaps
Frequent checkpoints for the assessment gaps are great for avoiding surprises. This keeps the team moving toward the end goals, and decisions are made to adjust the programs based on the feedback (example phased implementation of a Data Loss Prevention project to maximize the impact focusing on areas with a high volume of vulnerabilities first).
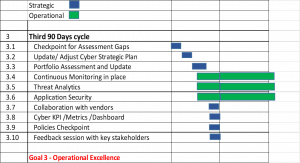
Figure 2: 3rd 90 days plan
Update/Adjust Cyber Strategic Plan
Based on the feedback from the board, which includes key stakeholders and internal teams, an update of the cyber strategy is highly recommended. The cyber strategy is a living document and should be revisited at least twice a year. Quarterly updates should be provided to key stakeholders for transparency and alignment.
Portfolio Assessment and Update
Portfolio status is an extremely critical, quarterly activity to keep the programs moving to ensure closure of the gaps and realization of business benefits. Program adjustments can be made based on the assessment results.
Continuous Monitoring in place
Continuous monitoring is the first step in operationalizing all the critical gaps as identified in the assessment. This provides a transparent representation of the operational measures against the policies and standards.
Threat Analytics
To obtain actionable intelligence, which can be shared with partners for effective action, threat intelligence is a critical aspect. This is achieved by using the business analytics component of the SIEM (security information and event management) platform, with the future of using an artificial intelligence platform in conjunction with SIEM.
Application Security
To improve the cybersecurity posture of the IT assets (application, data, middleware, network, compute and storage), cybersecurity checkpoints such as risk assessment, threat modeling, code inspection, and security testing are built into the organization’s delivery workflow. Key performance indicators (KPIs) from this workflow are used for leadership review for continuous improvement.
Collaboration with vendors
Vendors are an essential part of the cyber eco-system if managed well for value-added collaboration. A yearly performance assessment and discussion with vendor partners results in enhanced services, leveraging services and benefits for the operational teams. A critical deliverable of the cyber strategy should be a technology roadmap (impacting vendors).
cyberKPI/Metrics/Dashboard
A dashboard consisting of key performance indicators, preferably real-time and automated will highly valuable for decision making and reporting to the board. Dashboards can be detailed for the operational team and can be summarized for leadership and board. The cyberKPI can be dynamic and should be adjusted as cyber maturity improves.
Policies Checkpoint
Policy maturity to maintain compliance for the organization should be a critical task for this phase. Critical policies based on a standard cybersecurity framework such as NIST (National Institute of Standards and Technology), ISO (International Organization for Standardization), CIS (Center for Internet Security) should be formed and practiced by the organization.
Feedback session with key stakeholders
To achieve operational excellence, feedback sessions should be conducted with key stakeholders. I recommend capturing the output in a SWOT (Strength, Weakness, Opportunity and Threats) analysis. This is an objective way to document feedback, which can be applied for course correction as a key aspect of success.
Key Takeaways
- Continuous improvement is cyclic. Adopt the feedback to improve the journey.
- Develop an advisory committee consisting of stakeholders, industry peers and staff for well-rounded, 360-degree feedback.
Rajiv has more than 25 years of information technology strategy, operations, large systems integration, cybersecurity and program management experience. Rajiv is a principal with Plante Moran management Consulting, cybersecurity practice after serving as Chief Information Security Officer (CISO) for the Department of Technology, Management and Budget, State of Michigan.





Leave a Reply
You must be logged in to post a comment.