When you assemble a peanut butter sandwich, you want to spread the condiment evenly across your bread of choice. It doesn’t matter whether you’re a crunchy or smooth person, the consistent symmetrical coverage of the carb is key to an enjoyable sandwich experience.
However, when it comes to cybersecurity, agencies do not want to take a peanut butter perspective, where all systems, applications and data are covered or secured evenly.
“Our culture is used to the peanut butter approach, where we try to protect everything equally,” said Gerald Caron, Director of Enterprise Network Management at the State Department. This approach results in some systems being overprotected and overall network functionality being constrained. As the historic Prussian king Frederick the Great once said, he who defends everything defends nothing.
“With zero trust, we protect things most significant to us. The crown jewels, not the baloney sandwich,” Caron said at GovLoop’s “Transforming Government Security for a Cloud-Smart World” briefing center, a two-hour online training.
But this is just one piece of what zero trust encompasses. Zero trust has become something of a buzzword in recent years, so it’s important to understand what it actually is to implement this kind of security architecture.
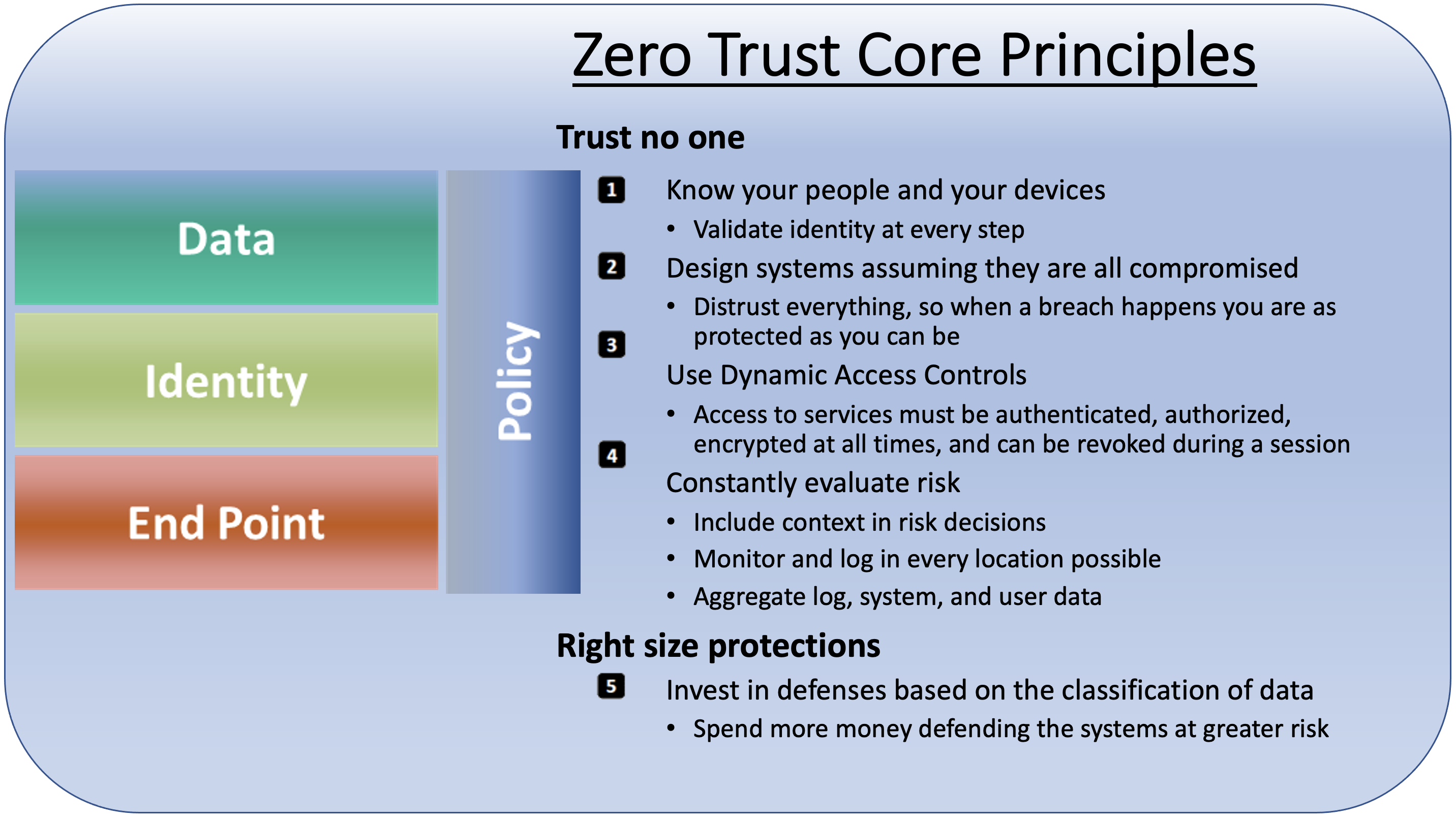
Its core principles can generally be broken into two: Trust no one, and tier protections.
Highlight: Data in Zero Trust
At the end of the day, agencies are ultimately trying to protect data through a zero-trust model, Caron said. Identity management controls and solutions are significant, but in the event that identity gets compromised, the first questions security teams ask are around data: What does the hacker have access to? Is there exfil, or data extraction?
A key part to understanding your data risk is understanding which data is important and not so important. For example, plans for holiday celebrations are not as sensitive and mission-critical as personally identifiable information (PII) on passport applications.
“Zero trust recognizes these differences and categorizes data based on its sensitivity and mission criticality,” Caron said in his presentation.
Again, it goes back to protecting your crown jewels over a baloney sandwich. “I’ll remake my baloney sandwich,” Caron said. You can’t remake the crown jewels.
As agencies put their data in the cloud, it’s all the more imperative to understand their data risk. Security certifications on cloud services, such as FedRAMP, mean little if agencies don’t take active ownership over their data protection.
“Do your homework, because at the end of the day, it’s still your data. … It’s not their data,” Caron said.





Leave a Reply
You must be logged in to post a comment.