Government agencies are ripe targets for cyberattacks, which are only evolving and getting worse over time. Adding to that challenge is the increase in remote work, with human error being the main cause of security breaches.
The biggest threat factor for data breaches is phishing. Cyberattacks often occur because someone made the decision to click on a bad link, or upload or download software they shouldn’t have, said G. Nagesh Rao, Acting Chief Information Officer (CIO) in the Bureau of Industry and Security at the Commerce Department. “And third party malicious actors are continually evolving trying to figure out how to poke the holes, and getting more and more sophisticated with their attacks.”
“IT security is important now more than ever…. There’s no room for failure when it come to people’s data and information,” Rao said.
Rao spoke alongside Matt Porco, Principle System Engineer at Citrix Public Sector, during GovLoop’s virtual summit on Wednesday. They discussed using artificial intelligence (AI) and machine learning (ML)-driven analytics solutions to detect and prevent security threats.
Considering this current landscape, IT security teams are typically short-staffed and overworked trying to keep agencies secure, Porco said. Whether that’s continuously monitoring suspicious user behavior or wiping users’ devices and applying more stringent security policies when attacks occur, an analytics solution can autonomously take care of these actions. It can also help reduce the manual labor that’s involved in keeping systems secure.
“The level of sophistication of AI and ML goes far beyond what we can do as regular people,” Porco said. Applying ML across multi-cloud infrastructure can detect patterns of bad behavior and help predict future issues.
Solution: Analytics
What are analytics and how do they help?
User behavior analytics is an ML-enabled process that monitors users over time to learn what each user’s “normal” behavior is, and then continuously monitors users to detect any abnormal behavior that deviates from the model.
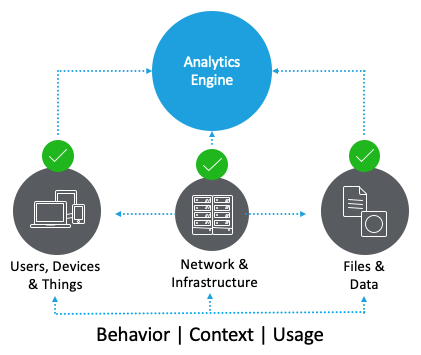
A good analytics system needs to be:
- Turn-key – agencies need simple data collection that can get comprehensive and diverse data from a lot of different sources easily.
- Accurate – false positives need to be reduced by correlating data from multiple vantage points.
- Autonomous – not every response needs to be a manual process, so the system needs to be able to take closed-loop autonomous actions in response to insights from monitoring user behavior.
When attendees at this online training were asked if their agency uses continuous monitoring, 55% of poll respondents said yes.
“Continuous monitoring is important because it is a key part of any zero trust security strategy,” Porco said, and zero trust is the direction that governments are moving in terms of their IT security strategy.
An Analytics Solution at Work
Citrix Analytics for Security
Citrix Analytics for Security is an AI/ML-driven user behavior analytics system that detects and mitigates threats from internal users. It focuses on easily identifying high-risk users.
Users are given a risk score of 0-100 (no-risk to high-risk) based on information from the different data sources that are sent to the Citrix Analytics service.
Once threats are identified, the system can respond by initiating closed-looped autonomous actions, such as blocking users from using their workspace or applying stricter security at the login level. The actions taken and risk level can be determined by the agency.
Here’s how IT security teams can deal with these real-world examples using analytics:
- Risky users – there is a risky users dashboard that will bring high-risk users to the top so they are easily viewable, this can be manual or an automated action taken by the system.
- Data exfiltration – a data exfiltration dashboard can show key data exfiltration methods that are being posed to the agency. The dashboard can also show primary risks, such as excessive file-sharing or unusual volume upload.
- Access failure – dashboards show trends of access failure so that IT can focus on where the attack is coming from.
Don’t miss out on other virtual learning opportunities. Pre-register for GovLoop’s remaining 2020 virtual summits today.






Leave a Reply
You must be logged in to post a comment.