 Transformation efforts play a key role in the ability of government entities to modernize their infrastructure, technology and business processes. Many organizations have undergone these types of projects or are currently in the implementation process. Research by McKinsey shows that there are common triggers which initiate a transformation effort as shown below:
Transformation efforts play a key role in the ability of government entities to modernize their infrastructure, technology and business processes. Many organizations have undergone these types of projects or are currently in the implementation process. Research by McKinsey shows that there are common triggers which initiate a transformation effort as shown below:
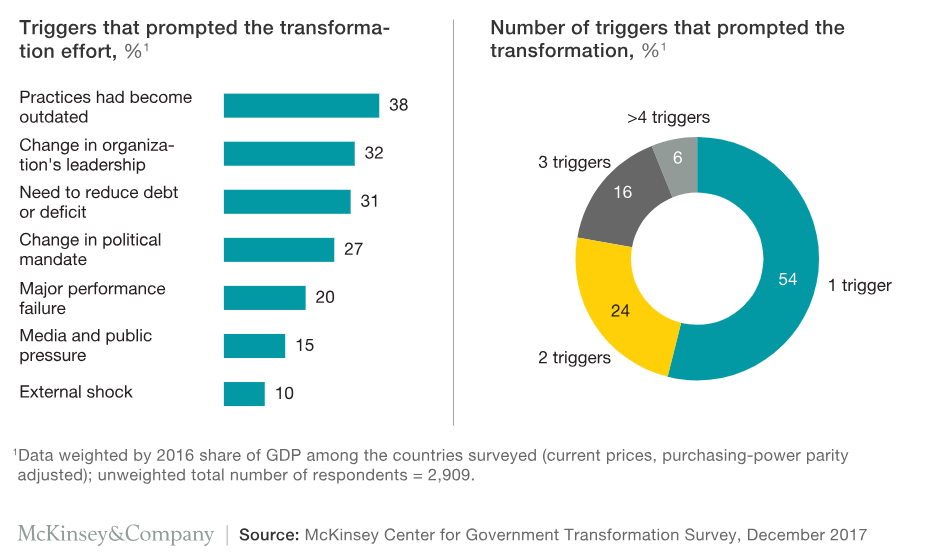
Some of the aforementioned triggers may be the result of a cybersecurity issue such as a breach or a new government regulation. Regardless of why organizations drive major change, it results in new cybersecurity risks. This presents new challenges that must be managed throughout with the program lifecycle.
A study by McKinsey found that about 80 percent of government transformation efforts fail. It is a daunting statistic for anyone championing such an effort. Each program situation is unique, but common themes that make or break the success of the project are consistent. This includes how cybersecurity fits into the transformation. Every project has five phases and cybersecurity efforts must be a part of all of them:
- Initiation
- Planning
- Execution
- Controlling
- Close Out
Initiation: The right stakeholders must be involved in the project charter process. The Chief Information Security Officer (CISO) and other cybersecurity leaders should be part of the decisionmaking at the project start. Setting the right tone at the beginning goes a long way to success in the later phases of the project.
Planning: Core cybersecurity requirements need to be identified along with all other project requirements. The early phases of the project are the most critical for intertwining the cybersecurity needs into the overall schedule and various work efforts. Cybersecurity requirements must be represented in the Work Breakdown Structure (WBS), scope and budget. Dedicated resources and budget should be assigned to cybersecurity aspects of the project. This will facilitate the proper engagement for cybersecurity to be integrated into the execution phase efforts.
Executing: Cybersecurity requirements should be implemented as new systems are developed, data migrated, or infrastructure replaced. Cybersecurity progress should be included in regular status reports. Daily engagement across teams is needed to implement the security controls and configurations or design secure processes.
Controlling: Key Performance Indicators (KPIs) for cybersecurity should be tracked and evaluated regularly with other program metrics. The WBS, forecasts and budgets must be updated along the way to ensure the right support is in place and appropriate progress is being made.
Close Out: As the transformation effort ends, all documentation related to cybersecurity design, architecture and operations and maintenance (O&M) are finalized and delivered. Conducting “lessons learned” sessions are important to understanding areas of improvement to leverage on future efforts.
Many of the common obstacles that organizations face are due to cybersecurity leaders and implementation considerations not being properly included at the beginning of the project. In other situations, cybersecurity may be seen as something that gets in the way of the delivery timeline. This results in cutting corners or improper prioritization and implementation of security requirements. Often, this only comes to light when there are shortcomings in the later project phases, during a third-party assessment organization (3PAO), or audit. Organizations with a culture of cybersecurity tend to have greater success avoiding or overcoming these challenges through effective and secure business practices.
Government organizations should be proud of a successful transformation effort. It is a major accomplishment. Given the risks and threats present today and those to come in the future, cybersecurity requirements and leaders must be involved in all aspects of the program.
Jason Yakencheck is part of the GovLoop Featured Contributor program, where we feature articles by government voices from all across the country (and world!). You can follow him on Twitter. To see more Featured Contributor posts, click here.





Leave a Reply
You must be logged in to post a comment.