That’s the question (ISC)2, a nonprofit education and certification organization, posed to more than 1,800 federal security professionals for its 2015 global workforce study. Nearly half of those surveyed — 47 percent — said government information security has not improved. A small but growing number of professionals —17 percent — said federal security is worse off. Here’s why:
- The government’s inability to keep pace with threats
- Poor understanding of risk management within government
- Inadequate funding for security initiatives
- Lack of qualified professionals available
“The findings reveal that despite significant investments in new cybersecurity policies, guidance and tools, the federal government’s state of security readiness suggests little return on its investment,” (ISC)2 said about the survey findings.
It’s worth noting that the government’s push to implement continuous monitoring tools and services across agencies is still rolling out. It has been less than five months since Congress passed a number of cybersecurity bills to shift from paper-based security reporting to a more automated and real-time awareness of security, to better define the responsibilities of agencies charged with defending the .gov domain and to bolster the Department of Homeland Security’s recruitment and retention of skilled cybersecurity professionals. The survey was conducted between October 2014 and January 2015.
“It takes a while to get things implemented,” said Dan Waddell, director of government affairs, National Capital Region, (ISC)2. “Up until a year ago, people were operating on two different sheets of music. These new initiatives are relatively new.”
The responses from federal professionals, which includes government and contractor employees, is part of the larger (ISC)2 2015 Global Information Security Workforce Study (GISWS) conducted by Frost & Sullivan. The global study includes input from nearly 14,000 information security professionals worldwide. The federal portion touches on a range of workforce issues, including workers’ top security concerns, cloud adoption and skills gaps in the security workforce. Results are compared with data from the 2013 version of the same study. I’ve included a few highlights from this year’s study.
Employee Compensation
We’ve all heard the argument that federal employees don’t make as much as contractors, and they certainly don’t make as much as their private sector counterparts. Well, that’s still true, according to the survey results. But the gap is shrinking. On average, federal security professionals reported making $110,500 a year, compared with $114,00 reported by contractors. The study notes that U.S. private sector employees make an average of $118,000 a year. (Note: 86 percent of the government and contractor survey respondents are male. Overall, they have an average of 15 years experience, and nearly half of them have advanced degrees).
A competitive salary is definitely one way to attract top talent, but “it’s not always about salary,” Waddell said. “One of the carrots is a robust training and education program,” adding that agencies need to do a better job of exploring other ways to compensate employees, not just salary.
One challenge facing agencies that needs to be addressed governmentwide is the hiring process, Waddell said. It takes months, unless agencies qualify for the direct hiring program, and the current process is bloated and bogged down by red tape. The lack of qualified professionals in government is having a negative impact on the existing workforce, agencies and their customers, the report noted.
Workforce Skills
To respond to the threat landscape over the next three years, security professionals said agencies need employees who understand risk assessment and management; incident investigation and response; governance, risk management and compliance. Communications skills also made the cut. Check out the complete list below.
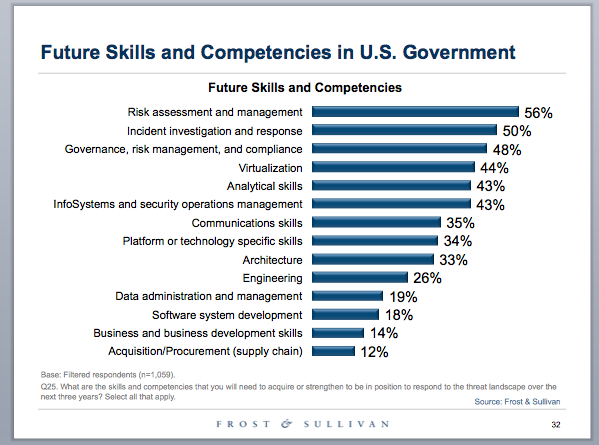
The shift to cloud computing is forcing agencies to re-evaluate the skills of their government and contractor workforce. When asked what skills will be required for dealing with cloud computing, participants noted more than a dozen new skills, including the ability to apply security controls to cloud environments; a knowledge of risks, vulnerabilities and threats; and service level agreement skills.
Cloud Migration Due to FedRAMP
When asked whether FedRAMP baseline security controls enabled their agency to migrate systems more securely to the cloud, 64 percent said they did not know. Those who said either yes or no were divided equally at 18 percent. One thing we do know, based on the report, is that an enhanced understanding of cloud security guidelines is one of the new skills professionals must acquire, in addition to those I listed earlier. And cloud security is still a top concern. Specifically, agencies are worried about data loss prevention, ensuring that existing IT security policy is replicated in the cloud, ensuring that data and systems meet continuity of operations guidelines, and integration of cloud and mobility.
One bright spot is that more security professionals view the Federal Risk and Authorization Management Program as an effective initiative today than they did two years ago. But not all of the necessary stakeholders are fully engaged with the program, and more training is needed. FedRAMP is hoping to change that through a series of free online training, multiagency working groups and other efforts. You can view those resources here.
There have been a lot of resources devoted to programs such as FedRAMP, rolling out the Cybersecurity Framework, and DHS’ Continuous Diagnostics and Mitigation program, but these are all relatively new programs, Waddell said. “We haven’t seen that great of an impact yet, hopefully that’s something we’ll see in the next survey.”





Leave a Reply
You must be logged in to post a comment.